01: How can use Item Level Targeting to apply a Group Policy Preferences or PolicyPak item when the user is NOT a member of Domain Admins and also is not a member of the local Admin group?
You might want to set a configuration item such that ONLY regular users and NOT “admins” are affected by a Group Policy Preferences or PolicyPak setting.
For example, perhaps you wish to “Prevent access to the command prompt” for all standard users, like what’s seen below, and you want to use Item Level Targeting to do it.

To clarify up front, Item Level Targeting is a Microsoft technology provided as part of the their Group Policy Preferences CSE for Group Policy.
PolicyPak utilizes this ability to filter based on criteria, but the underlying engine is developed by MS themselves. What that means is that its not our code and so sometimes there are behaviors related to ILT that we either are not aware of or have not yet tested.
Also, to better understand the challenge, here are some facts:
- All AD security groups and local groups outside of the Builtin domain groups have a unique SID that is unique to the AD domain for Domain based groups or the individual computer for local groups
- However, the Builtin Administrators group always has the same SID
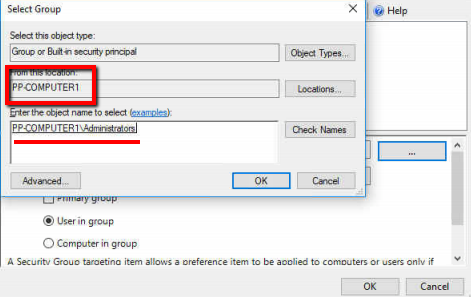
- Best practice when using a Security Group with ILT is to use the 3 dots and select the group itself, though this really only works for Domain based groups
- You CAN just type in the name of the group as we have discussed before, but this really only works for Domain based groups, it does NOT appear to work for local groups
- Therefore using the 3 dots on a machine and selecting a non-Builtin local group would really only work for that one machine and no others
- However, since the local Administrators group has the same SID on every computer, you CAN use this group, but not by just typing it in, you have to use the 3 dots to get its SID
And so with all that said, this is the combination that appears to work:


Three important things to note above
- We are using an "AND" instead of "OR"
- The Domain Admins group has been manually typed in "Domain Admins"
- But the Administrators local group I've clicked the 3 dots to select it and get its SID
The catch with the last item is that since there is no local Administrators group on a DC, a DC cannot see that group to add it, you must install the GPMC and the PP Admin Console on a regular machine (that is a member of the domain, so like a test W10 VM for example), edit the GPO and do the 3 dots, and then select the Computer name as the source, to capture the Administrators group that way.
You only have to do this once to get the group and its SID, but it just can't be done on a DC.
So after Clicking the 3 Dots….