8214
8214
Many organizations want to protect the data on the end-user’s computers from prying eyes. Especially laptops that may be virtually anywhere. BitLocker is an encryption feature built into computers running Window 10 Professional, Enterprise and Education that creates a secure environment for your data.
Deploying BitLocker to an enterprise can be a daunting task. Group Policy in combination with PolicyPak can automate the entire process with one GPO.
This document assumes the following
- Compatible version of Windows 10
- TPM present and enabled on the computer (TPM uses hardware level encryption to store BitLocker keys allowing zero-touch deployment and computer start-up)
Implement BitLocker
The instructions below will configure BitLocker to encrypt the used space on the SystemDrive with 256-bit encryption and save the Recovery Password and key to Active Directory. There are many more options that can be configured either through additional policies or customized script if so required.
- Create a Group Policy on the desired Domain / OU and Edit
- Expand Computer Configuration -> PolicyPak and click on Administrative Templates Manager
-
Add a new collection
- Give the Collection a descriptive name and, if required, set Item Level Targeting (ILT can filter the policy based on many different criteria including computer type (e.g. laptops), Operating System (e.g. Windows 10) or Security Group (e.g. Sales))
- Double-click to open the collection
-
Add a new Policy
- Browse to Windows Components and click on BitLocker Drive Encryption
-
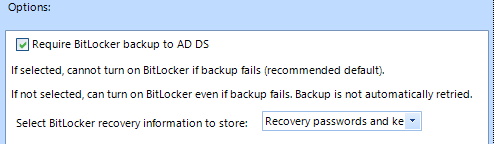
Open “Store BitLocker recovery information in Active Directory Domain Services (Windows Server 2008 and Windows Vista)” and set the following configuration
-
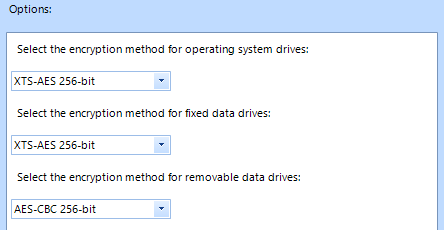
In the same location, open “Choose drive encryption method and cipher strength (Windows 10 [version 1511] and later) and set the following configuration
-
Click CLOSE
Note: If deploying different BitLocker configurations for different groups of users or computers, repeat steps 4 through 10 for each different configuration, setting the ILT on the collection to target your desired groupings.
- Still under PolicyPak, click on Scripts Manager
-
Add a new policy to start the Scripts Manager wizard
- Click NEXT
-
Select “Apply this policy to computer (default) and click NEXT
-
Configure “On apply action”
-
On the dropdown that says “(None)”, select “Batch Script” and type in the following text
Manage-bde -on %systemdrive% -Used
- Click NEXT
-
-
Configure “On revert action”
-
Select either “Once” or “Once or when forced” and click NEXT
- Give the policy a descriptive name and set Item Level Targeting if required
- Click FINISH
- Close Group Policy Management Editor
When the policy has been deployed to the user, they will receive a notification that a reboot will be required. It is not necessary that it be one immediately. Upon reboot BitLocker will automatically start to encrypt the drive with no input required from the user.